information security





Information Security Policy
kaonavi, Inc. (hereinafter the “Company") contributes to its clients through the kaonavi cloud-based human-resource management system.
The Company earns the trust of its clients and all stakeholders by protecting privacy and other human rights by securing information assets, including data on clients and other stakeholders, in addition to internal data, against various threats.
To do so, it has formulated the following Information Security Policy under which it implements safe and appropriate information security measures. All employees are made thoroughly aware of this Policy, which applies to all of the Company's various businesses.
1. Protection of information assets
The Company secures the confidentiality, integrity, and availability of information assets through appropriate organizational and technical measures. These measures include implementing management measures determined to be necessary to protect the various information assets, including those entrusted to us by our clients, as a result of risk assessment by the Company as a cloud service provider and as a cloud service customer.
2. Compliance with laws, regulations, and other rules
The Company complies with the requirements of laws, regulations, rules, and contracts concerning information security.
3. Access to information
The Company takes precautions to deter improper intervention in individuals' information. We cooperate with information-collection activities by national and local governments and other public agencies and similar parties only within the extent to which such cooperation is required.
4. Control of personal information
The Company handles important personal information in human resource operations appropriately and does not use it for other than its intended purposes.
5. Education and training
The Company provides the necessary education and training, as well as promoting thorough understanding of this Policy, to ensure that users of its information assets fully understand their importance.
6. Continual improvement
The Company periodically reviews the state of information security and various related rules and makes improvements as necessary.
kaonavi, Inc.
Hiroyuki Sato
Representative Director, President & Co-CEO
Established November 1, 2014
Revised December 22, 2022
Governance
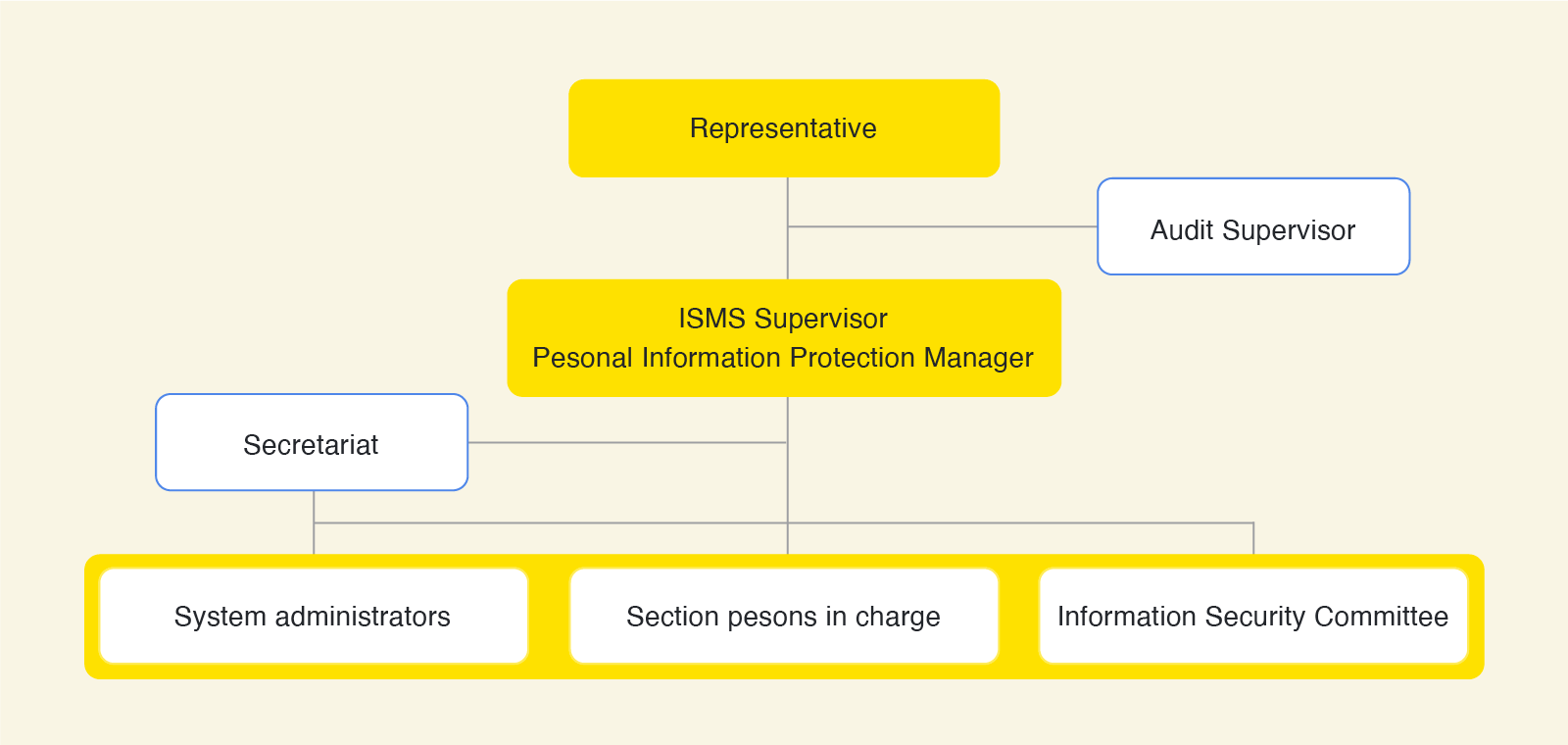
- To ensure that all executives and employees comply with and execute the Information Security Policy, we have appointed an Information Security Management System (ISMS) Supervisor and established an Information Security Committee.
- To ensure effective oversight by the Board of Directors, we have appointed an attorney specialized in data protection as an outside director (and Audit and Supervisory Board member).
- We conduct internal audits and accreditation audits by external agencies at least once a year.
Initiatives
- We formulate standards and rules regarding the persons responsible and persons in charge and their duties for each stage, including collection, use, retention, provision, and deletion/disposal of information.
- We implement risk assessments when new cases of information handling arise.
- We educate and train employees regarding points to note concerning handling of information, when they join the Company and at least once a year thereafter.
- We choose subcontractors that satisfy security requirements after first conducting prior subcontractor assessment.
- We limit accounts with access to information to the minimum necessary persons in charge as authorized by the Information Security Management System (ISMS) Supervisor and monitor logs of their use.
- We encrypt communication channels using Transport Layer Security (TLS 1.2), virtual private network (VPN), and other technologies, and we encrypt database data at the storage layer in data retention domains.
Accreditation
- The Company's kaonavi service has been accredited as a service that satisfies government security requirements under the Information system Security Management and Assessment Program (ISMAP) and is registered as an ISMAP cloud service.
- The Company has attained JIS Q 27001:2014(ISO/IEC 27001:2013) and JIP-ISMS517-1.0(ISO/IEC 27017:2015) certification.























